Client-Plugin Analysis
Investigation of risks posed by unofficial extensions (e.g. HTML plugins) and supply-chain aspects. Goal: demonstrate how attackers could theoretically exfiltrate data – with a focus on prevention and protection.
Focus on exploit development.
I work on exploit development and exploiting Windows devices.
Developing a modular security tooling framework (builder/automation), researching client plugins and server security, and producing clear reports.
Investigation of risks posed by unofficial extensions (e.g. HTML plugins) and supply-chain aspects. Goal: demonstrate how attackers could theoretically exfiltrate data – with a focus on prevention and protection.
Research showed that unofficial Discord client extensions (e.g. Vencord) combined with certain HTML plugins could, under unfavorable conditions, be abused to harvest credentials.
Creating minimal proofs-of-concept, reporting validated issues to operators (responsible disclosure) and recommending protections for domain control and content policies.
An assessment of a web application on a .GOV domain revealed a combination of misconfiguration in the domain/hosting context (domain control) and an XSS attack surface.
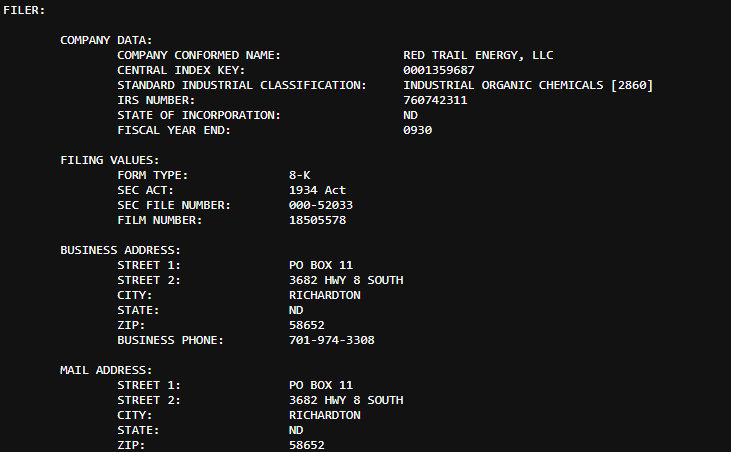
Structured reports, reproducible steps, impact assessment and cooperative communication with teams.
Modular tooling for security analysis and covert system monitoring. Focus on stealth and configurability, including the capability to execute arbitrary code.
A sandbox environment that enables testing potentially harmful software in a controlled setting, monitoring network activity and logging behavior in detail.

System administration and operational IT tasks.

Incident response activities (identity partially anonymized).
Classified document (released for viewing):
